Fortinet
Fortinet is a global leader and innovator in Network Security. Our mission is to deliver the most innovative, highest performing network security platform to secure and simplify your IT infrastructure. We are a provider of network security appliances and security subscription services for carriers, data centers, enterprises, distributed offices and MSSPs. Because of constant innovation of our custom ASICs, hardware systems, network software, management capabilities and security research, we have a large, rapidly growing and highly satisfied customer base, including the majority of the Fortune Global 100, and we continue to set the pace in the Network Security market. Our market position and solution effectiveness has been widely validated by industry analysts, independent testing labs, business organizations, and the media worldwide. Our broad product line of complementary solutions goes beyond Network Security to help secure the extended enterprise.
Fortinet is headquartered in Sunnyvale, California, with offices around the world. Founded in 2000 by Ken Xie, the visionary founder and former president and CEO of NetScreen, Fortinet is led by a strong and seasoned management team with deep experience in networking and security. For more information, visit our website at www.fortinet.com
-
04:12 Popular

FortiGate Cookbook - Logging W/ FortiCloud (5.2)
Added 267 Views / 0 LikesIn this example, you will use FortiCloud, an online logging service provided by Fortinet, to store the logs of your FortiGate unit’s traffic. You will also access logs using the FortiCloud website: http://www.forticloud.com/. Before you can use FortiCloud
-
05:34 Popular

FortiGate Cookbook - MAC Access Control (5.2)
Added 261 Views / 0 LikesIn this video, you will learn how to add device definitions to your FortiGate using Media Access Control addresses, or MAC addresses. These definitions form a whitelist that allow you to control the devices that can access your wireless network. MAC addre
-
02:36 Popular

FortiGate Cookbook - Packet Capture (5.2)
Added 392 Views / 0 LikesIn this video, you will learn how to use packet capture to monitor traffic passing through your FortiGate. Intercepting and capturing packets can be a useful troubleshooting tool, allowing you to analyze traffic in detail that has passed through your Fort
Featured -
02:47 Popular

FortiGate Cookbook - Port Forwarding (5.0)
Added 289 Views / 0 LikesIn this video, you're going to learn how to use virtual IPs to configure port forwarding on a FortiGate unit. Port forwarding allows you to 'open' ports and redirect traffic from one port to another. A variety of network services require open ports, such
-
03:39 Popular

FortiGate Cookbook - Port Forwarding (5.2)
Added 298 Views / 0 LikesIn this video, you will learn how to use port forwarding to limit access to an internal server. By using virtual IPs to configure port forwarding on your FortiGate unit, you can allow remote connections with a server behind the FortiGate’s firewall, but o
-
03:38 Popular

FortiGate Cookbook - Protect Server IPS/DoS (5.2)
Added 292 Views / 0 LikesIn this video, you will protect a web server against external attacks, using a FortiGate with an Intrusion Prevention System (IPS) profile and a Denial of Service (DoS) policy. This will defend your server against a variety of attacks. Before performing a
-
05:20 Popular

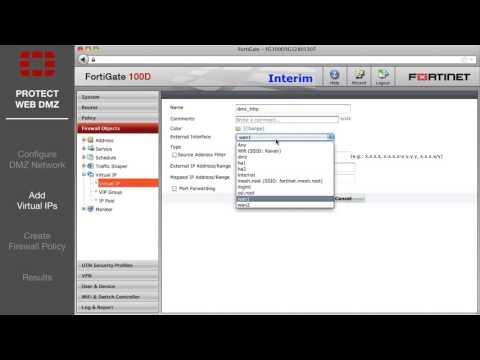
FortiGate Cookbook - Protect Web Server DMZ (5.2)
Added 267 Views / 0 LikesIn this video, you will learn how to configure a DMZ network to protect a public web server from unauthorized access. A DMZ network is a secure network connected to the FortiGate that only grants access if it has been explicitly allowed. In this example t
-
02:48 Popular

FortiGate Cookbook - Protecting A Web Server With DMZ (5.0)
Added 264 Views / 0 LikesIn this video, you're going to learn how to configure a DMZ network to protect a public web server from unauthorized access. A DMZ Network (from the term 'demilitarized zone') is a secure network connected to the FortiGate that only grants access if it ha
-
02:48 Popular

FortiGate Cookbook - Redundant Internet Connections (5.0)
Added 233 Views / 0 LikesIn this video, you're going to learn how to configure redundant internet connections from two ISPs on your FortiGate. Having two redundant internet connections can improve the reliability of your network by maintaining internet access in the event that on
-
05:03 Popular

FortiGate Cookbook - Redundant Internet Connections (5.2)
Added 260 Views / 0 LikesIn this video you will learn how to create a virtual Wide Area Network link that provides your FortiGate unit with redundant Internet connections from two Internet Service Providers or ISPs. The virtual WAN link combines both connections into a single int
-
05:01 Popular

FortiGate Cookbook - Remote Access With SSL VPN (5.0)
Added 260 Views / 0 LikesIn this video, you're going to learn how to configure SSL-VPN to allow a remote user to safely connect to a FortiGate-protected network, while enforcing the FortiGate's security policies for this user. An SSL-VPN tunnel allows users to remotely access a n
-
03:28 Popular

FortiGate Cookbook - Remote AP (5.0)
Added 299 Views / 0 LikesIn this video, you're going to learn how to use a Remote AP to provide secure remote access to protected networks and the internet. With the proper FortiGate configuration, a Wireless Access Point can be deployed remotely at home or anywhere outside your
-
06:04 Popular

FortiGate Cookbook - Remote Browsing With VPN (5.2)
Added 289 Views / 0 LikesIn this video, you will learn how to use remote IPsec and SSL VPN tunnels to bypass internet access restrictions. A VPN tunnel is an encrypted traffic passage between two endpoints. In this example, the VPN tunnel is between a local user running FortiClie
-
03:22 Popular

FortiGate Cookbook - Scheduled BYOD Access (5.2)
Added 230 Views / 0 LikesIn this video, you will learn how to limit mobile device access to a wireless network by setting up a schedule. By using a schedule group and a BYOD device policy, you can limit mobile device internet usage outside of set hours. BYOD, or Bring Your Own De
-
04:54 Popular
FortiGate Cookbook - Secure WiFi With A Captive Portal
Added 328 Views / 0 LikesProblem A FortiGate unit provides your office with wired networking, but employees also use laptops and mobile devices. These devices need secure WiFi access to both the office network and the Internet. The employees use web applications and are most comf
Featured -
05:08 Popular
FortiGate Cookbook - Secure WiFi With FortiAP
Added 294 Views / 0 LikesConfiguring a small office WiFi network by using a FortiGate unit to manage an FortiAP Remote WiFi access point. The WiFi network uses DHCP to assign IP addresses and WPA2-Personal security. WPA2-Personal security means there will be one preshared key tha
-
03:41 Popular
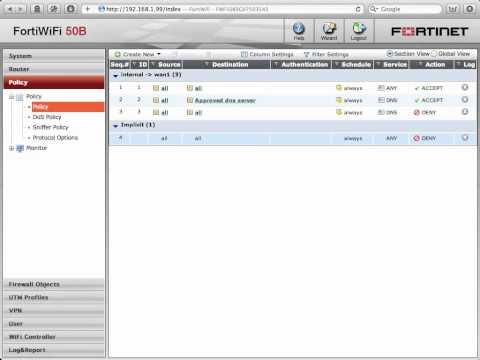
FortiGate Cookbook - Security Policies That Limit DNS Queries To Only One Approved DNS Server
Added 334 Views / 0 LikesCreate FortiGate security policies that block all DNS sessions except for sessions to the approved DNS server.
Featured -
03:09 Popular

FortiGate Cookbook - Site-to-Site IPsec VPN (5.2)
Added 331 Views / 0 LikesIn this video, you will create a route-based IPsec VPN to allow transparent communication between two different networks, each located behind a FortiGate. The VPN will be created on both FortiGates by using the VPN Wizard’s Site to Site FortiGate template
Featured -
03:25 Popular

FortiGate Cookbook - SSL Certificate Warnings (5.2)
Added 225 Views / 0 LikesIn this video, you will learn how to prevent your users from getting security certificate errors when you have full SSL inspection (also known as deep inspection) enabled. By providing users with the FortiGate SSL CA certificate, you will discourage them