Fortinet
Fortinet is a global leader and innovator in Network Security. Our mission is to deliver the most innovative, highest performing network security platform to secure and simplify your IT infrastructure. We are a provider of network security appliances and security subscription services for carriers, data centers, enterprises, distributed offices and MSSPs. Because of constant innovation of our custom ASICs, hardware systems, network software, management capabilities and security research, we have a large, rapidly growing and highly satisfied customer base, including the majority of the Fortune Global 100, and we continue to set the pace in the Network Security market. Our market position and solution effectiveness has been widely validated by industry analysts, independent testing labs, business organizations, and the media worldwide. Our broad product line of complementary solutions goes beyond Network Security to help secure the extended enterprise.
Fortinet is headquartered in Sunnyvale, California, with offices around the world. Founded in 2000 by Ken Xie, the visionary founder and former president and CEO of NetScreen, Fortinet is led by a strong and seasoned management team with deep experience in networking and security. For more information, visit our website at www.fortinet.com
-
02:32 Popular

FortiGate (FortiExplorer): So Easy A Kid Can Set It Up
Added 613 Views / 0 LikesThe FortiExplorer is a utility, which provides an easy way for setup and configuration of a Fortinet FortiGate. It is so easy, where a 7 year old can setup a security gateway.
Featured -
03:41 Popular

FortiGate Cookbook - Two-Factor Auth W/ SSL And FortiToken (5.0)
Added 606 Views / 0 LikesIn this video, you're going to learn how to set up two-factor authentication for an SSL VPN user, using FortiToken. An SSLVPN connection can use two-factor user authentication for enhanced security, requiring the user to present a secondary credential to
Featured -
01:31 Popular
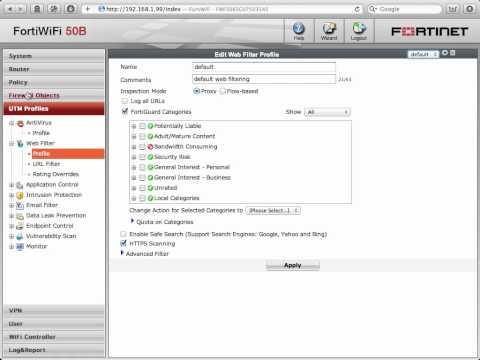
FortiGate Cookbook - Limiting The Types Of Web Sites Users Can Visit
Added 604 Views / 0 LikesConfigure FortiGuard Web Filtering to block access to websites that consume excessive network bandwidth.
Featured -
04:54 Popular
FortiGate Cookbook - Secure WiFi With A Captive Portal
Added 600 Views / 0 LikesProblem A FortiGate unit provides your office with wired networking, but employees also use laptops and mobile devices. These devices need secure WiFi access to both the office network and the Internet. The employees use web applications and are most comf
Featured -
10:22 Popular

Cookbook - SSL VPN W/ Certificate Auth (5.2)
Added 597 Views / 0 LikesIn this video, you will configure an SSL VPN tunnel that requires users to authenticate with a certificate. The certificate, username, and password are used for two-factor authentication. When authorized users connect through the SSL VPN tunnel, the Forti
Featured -
02:36 Popular

Fortinet Network Security Academy | Solving The Cyber Security Skills Shortage
Added 596 Views / 0 LikesExplore Fortinet’s Network Security Expert program: https://training.fortinet.com/local/staticpage/view.php?page=nse Join the Fortinet Network Security Academy: https://www.fortinet.com/support/training/network-security-academy-form.html See how Fortinet’
Featured -
05:05 Popular

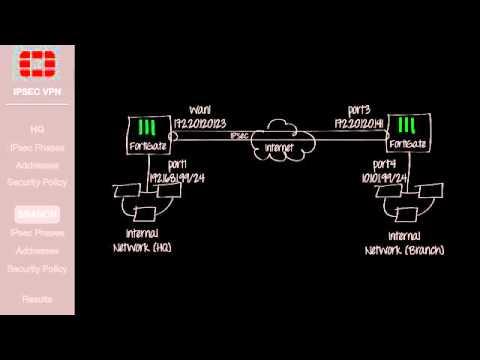
FortiGate Cookbook - IPsec VPN W/ Overlapping Subnets (5.2)
Added 595 Views / 0 LikesIn this video, you will learn how to construct a site-to-site IPsec VPN connection between two networks with overlapping subnets. Without the proper configuration, connecting two networks with overlapping subnets can lead to IP conflicts and traffic error
Featured -
04:26 Popular
IPsec VPN Two Factor Auth With FortiToken 5 4
Added 595 Views / 0 LikesFortinet made a pretty good video explaining how to setup IPSEC VPN's with two factor authentication when using FortiToken 5.4 Check out the video and be sure to check out http://www.fortinetguru.com for the best tips on Fortinet Hardware and how to utili
Featured -
05:24 Popular

FortiGate Cookbook - Basic FortiGate Setup (6.0)
Added 595 Views / 0 LikesMore on FortiGate setups: https://cookbook.fortinet.com/basic-fortigate-network-collection-60/index.html Learn more about FortiOS: https://www.fortinet.com/resources.html Explore Fortinet Security Fabric capabilities: https://www.fortinet.com/solutions/en
Featured -
01:38 Popular
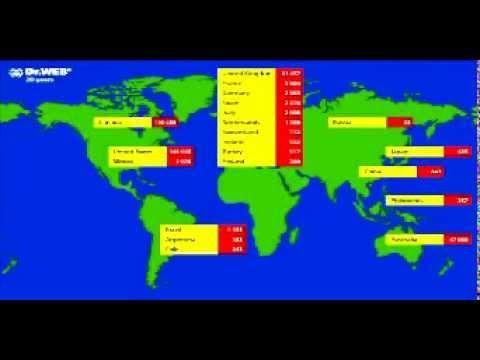
"Flashback" Mac Malware
Added 595 Views / 0 LikesGuillaume Lovet en conversation avec Radio Classique sur le sujet du malware "Flashback" pour les Macs Guillaume Lovet in conversation with Radio Classic on the subject of the "Flashback" Mac Malware
Featured -
06:42 Popular
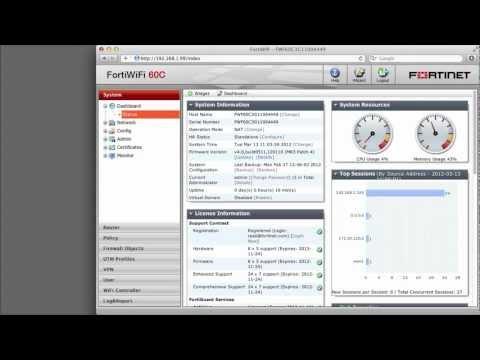
FortiGate Cookbook - Using The FortiClient VPN To Set Up A VPN Between A User And A Private Network
Added 592 Views / 0 LikesIn this example, user sgreen is part of the Wizard_Users usergroup. Once the VPN tunnel is up, sgreen's FortiClient Connect will be assigned an IP address in the range 192.168.1.[90-99]. If there are multiple devices sharing the VPN tunnel they will use t
Featured -
03:09 Popular

FortiGate Cookbook - Site-to-Site IPsec VPN (5.2)
Added 592 Views / 0 LikesIn this video, you will create a route-based IPsec VPN to allow transparent communication between two different networks, each located behind a FortiGate. The VPN will be created on both FortiGates by using the VPN Wizard’s Site to Site FortiGate template
Featured -
09:09 Popular

Cookbook - Social WiFi Captive Portal With FAC (4.0) - Twitter
Added 592 Views / 0 LikesThis video shows you how to configure an API for Twitter accounts, set up a portal RADIUS service on the FortiAuthenticator, and configure the FortiGate for Captive Portal access. Visit Fortinet's documentation library at http://docs.fortinet.com or our c
Featured -
04:31 Popular
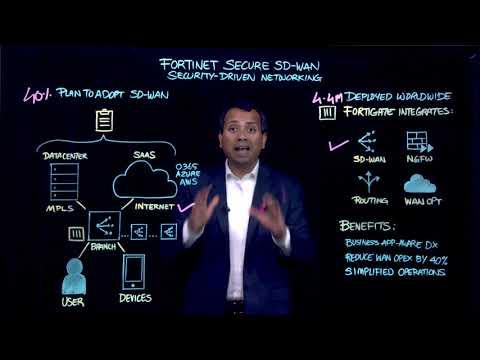
Fortinet Secure SD-WAN: Software-Defined WAN Explained. | Security Driven Networking
Added 590 Views / 0 LikesMore Fortinet Lightboard Videos: https://www.youtube.com/watch?v=ZxBBgbD6pmQ&list=PLLbbcH8MnXJ49bqBqjZzYNGx8HHwPf3x_ What is SD-WAN? https://www.fortinet.com/products/sd-wan.html Related videos: Fortinet Secure SD-WAN | Branch Network Security: https://ww
Featured -
03:41 Popular
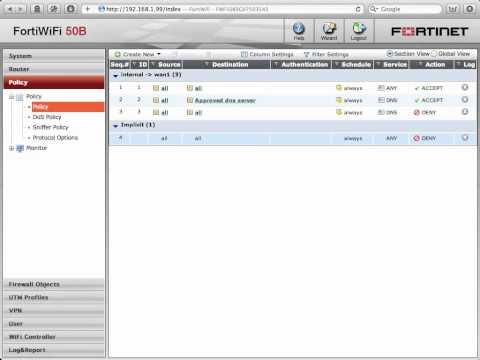
FortiGate Cookbook - Security Policies That Limit DNS Queries To Only One Approved DNS Server
Added 585 Views / 0 LikesCreate FortiGate security policies that block all DNS sessions except for sessions to the approved DNS server.
Featured -
03:39 Popular

FortiGate Cookbook - Port Forwarding (5.2)
Added 582 Views / 0 LikesIn this video, you will learn how to use port forwarding to limit access to an internal server. By using virtual IPs to configure port forwarding on your FortiGate unit, you can allow remote connections with a server behind the FortiGate’s firewall, but o
Featured -
03:32 Popular

FortiGate Cookbook FortiGate And FortiAP 5 0 01 21
Added 580 Views / 0 Likeshttps://plus.google.com/+charlyprudent/ nosql-database.org www.couchbase.com http://www.network-engineer.usa.cc http://www.crunchbase.com/person/charly-prudent https://github.com/charlyprudent
Featured -
04:13 Popular

FortiGate Cookbook - Blocking Windows XP Traffic (5.2)
Added 579 Views / 0 LikesIn this video, you will learn how to use Application Control to block web traffic from devices running Windows operating systems in the NT5 category, including Windows XP and Windows Server 2003, and virtual machines of these OSs. When an operating system
Featured