Fortinet
Fortinet is a global leader and innovator in Network Security. Our mission is to deliver the most innovative, highest performing network security platform to secure and simplify your IT infrastructure. We are a provider of network security appliances and security subscription services for carriers, data centers, enterprises, distributed offices and MSSPs. Because of constant innovation of our custom ASICs, hardware systems, network software, management capabilities and security research, we have a large, rapidly growing and highly satisfied customer base, including the majority of the Fortune Global 100, and we continue to set the pace in the Network Security market. Our market position and solution effectiveness has been widely validated by industry analysts, independent testing labs, business organizations, and the media worldwide. Our broad product line of complementary solutions goes beyond Network Security to help secure the extended enterprise.
Fortinet is headquartered in Sunnyvale, California, with offices around the world. Founded in 2000 by Ken Xie, the visionary founder and former president and CEO of NetScreen, Fortinet is led by a strong and seasoned management team with deep experience in networking and security. For more information, visit our website at www.fortinet.com
-
27:01 Popular

Ken Xie: A Security-Driven Network For A Hyperconnected World | Fortinet Accelerate 2019
Added 516 Views / 0 LikesLearn more: https://www.fortinet.com/corporate/about-us/newsroom/press-releases/2019/fortinet-expands-its-security-fabric-to-advance-the-third-genera.html https://secure.fortinet.com/LP=6225?utm_source=social&utm_medium=youtube&utm_campaign=GEN-WP-Three-U
Featured -
08:28 Popular
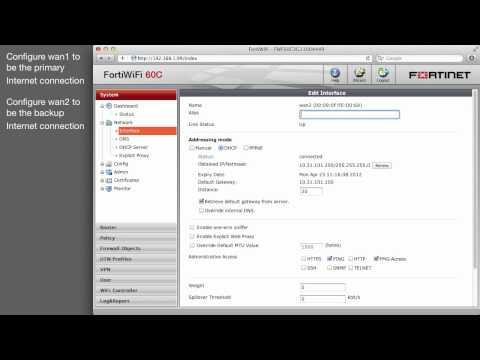
Cookbook - Installing Dual Internet
Added 514 Views / 0 LikesHow to install a redundant internet connection on the FortiGate.
Featured -
04:03 Popular

Fortinet Security Minute Sept 2011
Added 514 Views / 0 LikesThis month Fortinet senior security strategist, Derek Manky, talks about latest threats posed by "Anonymous," Microsoft's help in taking down the Waledac botnet and new malware discovered on Android phones.
Featured -
01:20 Popular

Fortinet's Secure Access Solution | Security-Driven Networking
Added 514 Views / 0 LikesLearn more: https://www.fortinet.com/solutions/enterprise-midsize-business/secure-access.html How the Security Fabric supports business-critical services: https://www.youtube.com/watch?v=Rr5XkPgyHh8 More on how Fortinet solutions secure business initiativ
Featured -
03:42 Popular

FortiGate Cookbook - IPsec VPN For Remote IOS Users (5.2)
Added 509 Views / 0 LikesIn this video, you're going to learn how to set up an IPsec VPN using the new VPN Wizard in FortiOS 5.2. Using IPsec VPN, you can provide remote iOS users with secure, encrypted access to an internal network, and routes their Internet traffic through the
Featured -
02:38 Popular
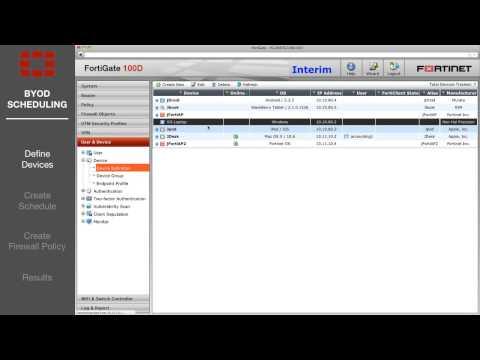
FortiGate Cookbook BYOD Scheduling 5 0 01 21
Added 509 Views / 0 Likeshttps://plus.google.com/+charlyprudent/ nosql-database.org www.couchbase.com http://www.network-engineer.usa.cc http://www.crunchbase.com/person/charly-prudent https://github.com/charlyprudent
Featured -
04:56 Popular

FortiGate Cookbook - Blocking Tor Browsing (5.2)
Added 508 Views / 0 LikesIn this video, you will grant a Tor Browser user access to the internet, while monitoring the user's activity. Use of the Tor Browser will be blocked for all other users. Tor, or The Onion Router, allows users to bounce their traffic around a distributed
Featured -
00:58 Popular

Welcome To Fortinet | Fortinet APAC Team
Added 508 Views / 0 LikesFor more information: https://www.fortinet.com/corporate/about-us/about-us.html Check out job opportunities in Fortinet APAC: https://www.fortinet.com/corporate/careers.html
Featured -
02:48 Popular
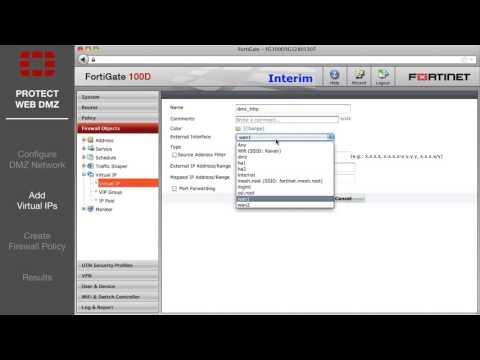
FortiGate Cookbook - Protecting A Web Server With DMZ
Added 505 Views / 0 LikesFeatured -
02:42 Popular
FakeMart : Le Virus Android Francais
Added 505 Views / 0 LikesAxelle Apvrille explique les erreurs de code qui ont contribué à la découverte d'Android/FakeMart - un malware qui a causé un prejudice de 500 000 euros. Axelle Apvrille explains code errors that helped in the discovery of Android/FakeMart - a malware tha
Featured -
13:20 Popular
FortiGate Secure Web Gateway Demo | Network Security
Added 505 Views / 0 LikesLearn more: https://www.fortinet.com/products/secure-web-gateway.html Fortinet Secure Web Gateway defends users from Internet-borne threats and helps enterprises enforce policy compliance for internet applications. With FortiGate SWG, you can deploy indus
Featured -
10:10 Popular

La Cyberattaque Sur L'Elysée
Added 504 Views / 0 LikesL'interview de Guillaume Lovet avec RCI sur le cyberattaque dont a été victime l'Elysée. Guillaume Lovet's interview with RCI on the cyberattack that the Elysee fell victim to.
Featured -
02:30 Popular
A Working Demonstration Of AndroRat With Audio
Added 502 Views / 0 LikesMore details can be found at the related blog post : http://blog.fortinet.com/Mobile-RAT-Infestation/ Video by : Ruchna Nigam Voice : Patrick Grillo
Featured -
02:36 Popular

FortiGate Cookbook - Explicit Web Proxy (5.0)
Added 501 Views / 0 LikesIn this video, you're going to learn how to set up the FortiGate Explicit Web Proxy to allow users on your internal network to browse the web through a web proxy. By also enabling web caching for web proxy users, you can speed up web browsing for your use
Featured -
03:20 Popular
FortiGate Cookbook Blocking Oversize File Downloads 5 0
Added 501 Views / 0 LikesFeatured -
05:36 Popular

Fortinet - A History Of Innovation
Added 501 Views / 0 LikesAs Fortinet continues to celebrate its 10 Year Anniversary, Ken Xie details the company's history, growth and innovation, while employees discuss their company experiences.
Featured -
01:38 Popular

Zero-Trust Network Access: Security In An Evolving Threat Landscape | Fortinet
Added 501 Views / 0 LikesLearn more: https://www.fortinet.com/blog/business-and-technology/know-who-and-what-with-zero-trust-network-access Explore Fortinet network access control solutions: https://www.fortinet.com/products/network-access-control Listen to Fortinet CISOs Jonatha
Featured -
00:31 Popular

Foscam Persistent XSS Vulnerability
Added 500 Views / 0 LikesMore details at : http://blog.fortinet.com/post/stored-xss-vulnerabilites-on-foscam-3 FortiGuard Advisory : http://fortiguard.com/advisory/fortinet-discovers-foscam-stored-xss-vulnerabilities
Featured -
08:48 Popular

FortiGate Cookbook - VDOM Configuration (5.2)
Added 499 Views / 0 LikesIn this video, you will learn how use Virtual Domains or VDOMs to host two FortiOS instances on a single FortiGate unit. Virtual Domains (VDOMS) can be used to divide a single FortiGate unit into two or more virtual instances of FortiOS. These instances f
Featured





