Juniper Networks
We believe the network is the single greatest vehicle for knowledge, collaboration, and human advancement that the world has ever known. Now more than ever, the world relies on high-performance networks. And now more than ever, the world needs network innovation to unleash our full potential.
Every day, Juniper Networks is helping our customers build the best networks on the planet. Every innovation we envision, every technology we create is informed by our desire to help solve our customers’ toughest challenges so they can compete and thrive today and into the future.
For more information, visit our website www.juniper.net
-
02:05 Popular

Juniper Networks Security Director - (French)
Added 444 Views / 0 LikesJuniper Networks Security Director est une plate-forme de gestion de la sécurité physique et virtuelle consolidée qui permet une application, la visibilité et intelligence décisionnelle.
Featured -
02:14 Popular

Data Center Rap Battle: On Demand Vs Always On
Added 444 Views / 0 LikesDave is all about virtualization, the cloud and deploying the next big money-making app or service. But if Nick from IT knows one thing, it's that a security breach means the entire company is down for the count. Sure, they've struggled in the past, but n
Featured -
02:10 Popular

Juniper Networks QFX5100 Top-of-Rack Switches
Added 444 Views / 0 LikesThe Juniper Networks QFX5100 line is the latest addition to Juniper's data center switch family. TheQFX5100 are the world's most nimble top-of-rack switches, supporting a number of configuration options and deployment scenarios designed to satisfy the nee
Featured -
12:36 Popular
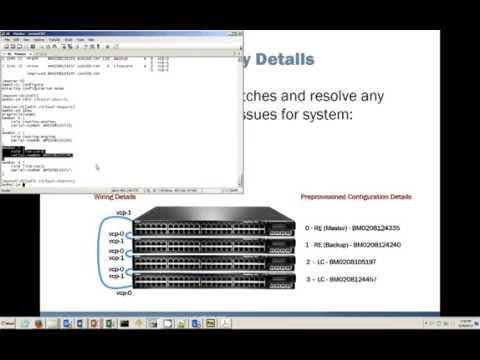
Virtual Chassis Troubleshooting
Added 443 Views / 0 LikesA Virtual Chassis is a collection of Juniper Networks EX and QFX Series switches that are interconnected and appear and can be managed as a single entity. The Virtual Chassis Troubleshooting Learning Byte is appropriate for users deploying a Virtual Chass
Featured -
10:04 Popular
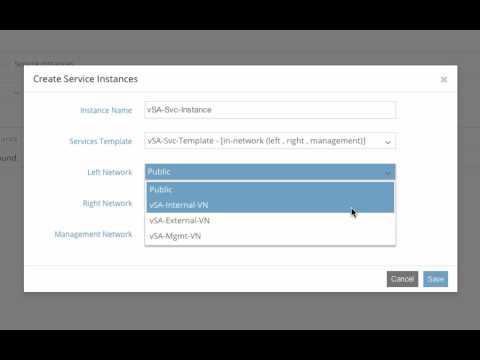
Elastic SSL VPN Service Over Contrail For Secure Mobile Connectivity
Added 443 Views / 0 LikesThis video showcases Contrail as a powerful platform to enable elastic and agile deployment of SSL VPN service to significantly facilitate secure mobile connections to enterprise critical resources and applications to accommodate the increasingly mobile a
Featured -
13:26 Popular
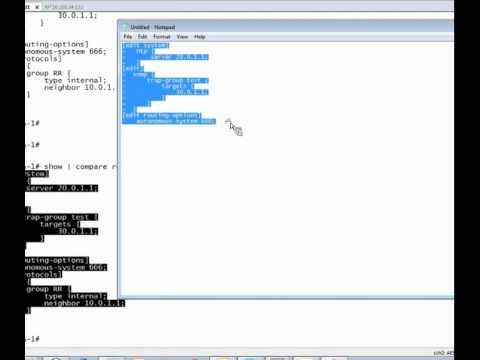
Junos CLI Advanced Techniques: Load Patch And Replace Pattern Learning Byte
Added 443 Views / 0 LikesThe Advanced CLI Techniques Learning Byte provides an overview of two very powerful commands - 'load patch' and 'replace pattern' The techniques revealed in this Learning Byte are extremely useful for those wishing to accomplish more in a shorter period o
Featured -
09:04 Popular
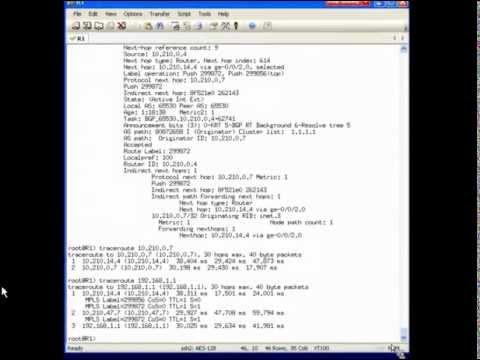
Juniper MPLS Basics Learning Byte
Added 442 Views / 0 LikesThe MPLS Basics Learning Byte covers basic steps for initial MPLS configuration in the Junos OS. This byte is most appropriate for users who are just beginning to use MPLS features of the Junos OS, or anyone looking for a quick-start guide for basic MPLS
Featured -
02:29 Popular
Set The Foundation For Mobile Growth While Reducing Transport Costs
Added 442 Views / 0 LikesAdd more customers, drop less calls. Achieve both with a healthy bottom line. Juniper's Mobile Backhaul Solution. The ACX Series Universal Access Router anchors the first fully integrated, end-to-end mobile backhaul architecture. And, the MX Series Univer
Featured -
04:03 Popular
Virtual Chassis Technology For The Campus
Added 442 Views / 0 LikesSee how Juniper's Virtual Chassis Technology can create a simpler, easier to manage campus network. Virtual Chassis technology increases availability, reduces network latency, improves bandwidth utilization, and simplifies network management. The result i
Featured -
05:32 Popular

Hoff's Security Bulletin: Active Defense Security
Added 441 Views / 0 LikesSr. Director of Security Strategy Chris Hoff discusses active defensive security that involves preemptive and counter strikes or hacking back.
Featured -
05:46 Popular

Service Automation -- Reducing Then Time To Solve Issues
Added 441 Views / 0 LikesIn the fifth and final video of the networking lifecycle series, Joe Robertson takes a look at service automation. With the ever increasing complexity of today's networks Joe discusses how you can free up staff from tedious routine tasks so they can focus
Featured -
00:51 Popular

Mobility - The Juniper Approach
Added 440 Views / 0 LikesMobility has caused a seismic shift—service providers are realizing it's becoming the primary vehicle for delivering experiences users want. Enterprises are looking to use it to enable their workforce. In this video, Mike Marcellin, SVP of Strategy and Ma
Featured -
01:27 Popular

The New Network: Video Commercial
Added 440 Views / 0 LikesLearn More: http://www.juniper.net/us/en/dm/choice/ The new network is here - Connect everything. Empower everyone.
Featured -
03:34 Popular

Virtual Revolution. Real Profits. - Korean
Added 440 Views / 0 Likes비디오 설명 : 개인화의 시대가 도래함에 따라 실시간으로 맞춤형 서비스가 주문되고 고객들께 전달되어 집니다. 반면에 레가시 네트워크는 너무 견고하고 느리면서도 변경에 드는 비용이 매우 비쌉니다. 이것은 고객만족을 낮추고 이익율을 감소시킵니다. 변화는 저절로 오는 것이 아니라 네트워크 가상화 기술을 통해서 지금 바로 실현 될 수 있습니다. 서비스를 만들어 내고 고객께 보다 빠르게 전달 해 보십시오. 여러분의 네트워크 진화를 비즈니스 만큼이나 빠르게 구축
Featured -
09:48 Popular

The State Of NFV
Added 440 Views / 0 LikesJoin Heavy Reading Senior Analyst Caroline Chappell and Juniper VP Product Marketing Paul Obsitnik as they review the state of the industry with Network Functions Virtualization (NFV). NFV is enabling a transformation unlike other transitions we've seen b
Featured -
01:13 Popular

SDN & NFV? It’s Child’s Play – Proof Of Concept 2 Of 4
Added 439 Views / 0 LikesThis video looks at some of the issues service providers must consider at the Proof of Concept stage of their SDN and NFV journey. It does so in a light hearted way by using child actors to replay conversations that occur during a typical proof of concept
Featured -
12:02 Popular
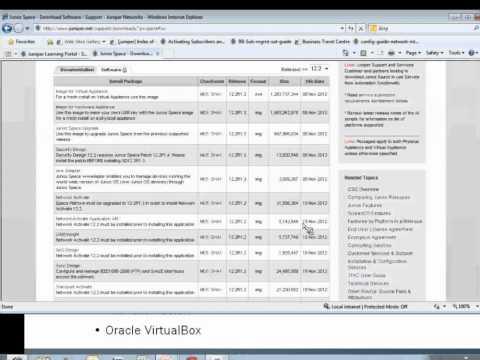
Junos Space Initial Install Learning Byte
Added 439 Views / 0 LikesThe Junos Space Initial Install learning byte describes the two Junos appliances—the physical appliance and the virtual appliance—and describes the requirements for installing the virtual appliance. The Learning Byte further describes setup and configurat
Featured -
00:55 Popular
![Junos Spotlight Elevator Pitch - [dutch]](https://www.telecomvideos.com/uploads/thumbs/5a49d67c3-1.jpg)
Junos Spotlight Elevator Pitch - [dutch]
Added 439 Views / 0 LikesJunos Spotlight is een database waarin hackers informatie verzameld wordt, welke vervolgens gedeeld kan worden tussen verschillende klantsystemen. Deze nieuwe manier van het in kaart brengen van "bad actors" verandert het spel tussen aanvaller en verdedig
Featured -
02:22 Popular
Présentation De La Solution Campus
Added 439 Views / 0 LikesPrésentation de la solution Campus
Featured





